OBSCURE#BAT malware marketing campaign exploits social engineering & pretend software program downloads to evade detection, steal information and persist on techniques. Learn to keep protected.
Cybersecurity researchers at Securonix Risk Labs have noticed a brand new malware marketing campaign referred to as OBSCURE#BAT. This marketing campaign makes use of social engineering tactics and faux software program downloads to trick customers into executing malicious code, enabling attackers to contaminate techniques and keep away from detection.
The assault begins with a person executing a malicious batch file, which is commonly disguised as reliable safety features or malicious software program downloads. As soon as executed, the malware establishes itself by creating scheduled duties and modifying the Home windows Registry to function even after the system reboots.
The malware then makes use of a user-mode rootkit to cover its presence on the system, making it troublesome for customers and safety instruments to detect. The rootkit can conceal recordsdata, registry entries, and working processes, permitting the malware to embed additional into reliable system processes and companies.
Faux Captchas and Malicious Software program Downloads
As seen in recent similar campaigns, hackers have been leveraging typosquatting and social engineering techniques to current pretend merchandise as reliable inside their provide chains. This consists of:
Masquerading Software program: Attackers additionally disguise their malicious recordsdata as reliable purposes, akin to Tor Browser, SIP (VoIP) software program or Adobe merchandise, growing the possibilities that customers will execute them.
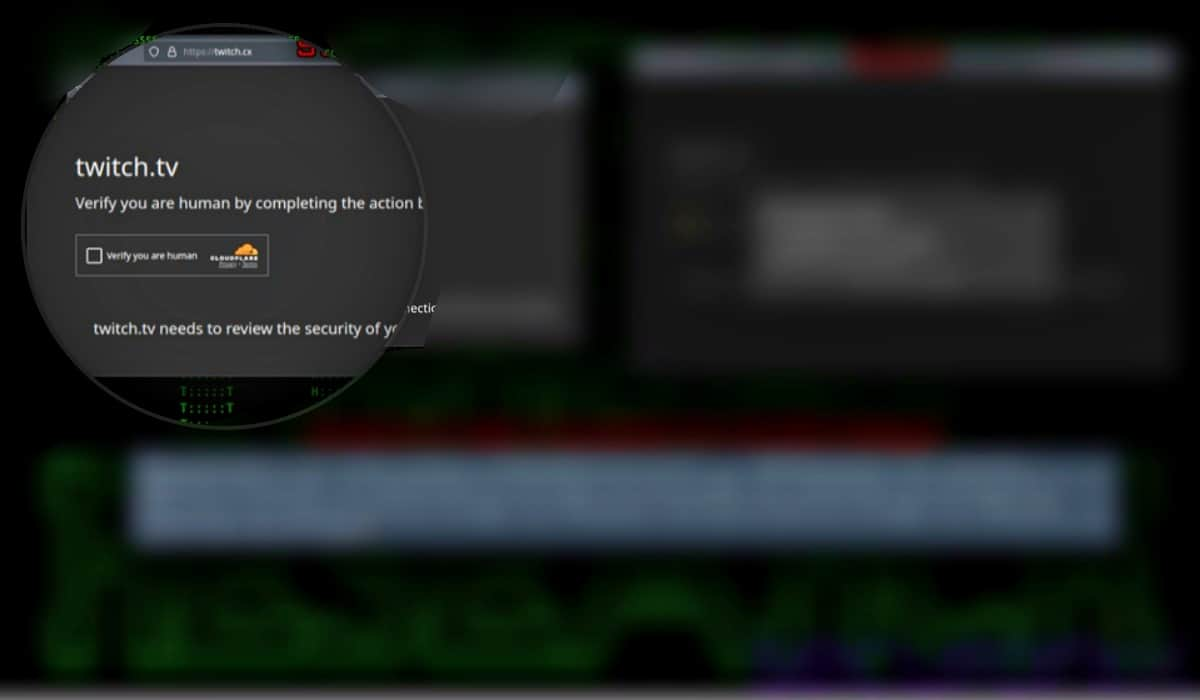
Faux Captchas: Customers might encounter a fake captcha, particularly the Cloudflare captcha characteristic, that methods them into executing malicious code. These captchas usually originate from typosquatted domains, resembling reliable websites. When customers try to move the captcha, they’re prompted to execute code that has been copied to their clipboard.
Evasion Strategies
The OBSCURE#BAT malware marketing campaign is a significant cybersecurity risk to each people and organizations, primarily attributable to its skill to compromise delicate information by superior evasion methods. These embrace:
API Hooking: Through the use of user-mode API hooking, the malware can conceal recordsdata, registry entries, and working processes. Which means that frequent instruments like Home windows Job Supervisor and command-line instructions can’t see sure recordsdata or processes, significantly those who match a selected naming scheme (e.g., these beginning with “$nya-“).
Registry Manipulation: It registers a pretend driver (ACPIx86.sys) within the registry to make sure additional persistence. This driver is linked to a Home windows service, permitting it to execute malicious code with out elevating suspicion.
Stealthy Logging: The malware displays person interactions, akin to clipboard exercise, and commonly writes this information to encrypted recordsdata, additional complicating detection and evaluation.
Nations Focused within the OBSCURE#BAT Assault
In accordance with Securonix’s detailed technical report, shared with Hackread.com earlier than its official launch on Thursday, the malware seems to be financially motivated or geared toward espionage, focusing on customers primarily within the following nations:
- Canada
- Germany
- United States
- United Kingdom
Shield Your self from the OBSCURE#BAT Assault
Whereas frequent sense is a should when downloading software program or clicking on unknown hyperlinks, customers and organizations also needs to observe these key safety measures to guard their techniques from OBSCURE#BAT and comparable threats:
- Clear downloads: Solely obtain software program from reliable web sites, and be cautious of pretend captchas and different social engineering techniques.
- Use endpoint logging: For organizations, deploy endpoint logging instruments, akin to Sysmon and PowerShell logging, to reinforce detection and response capabilities.
- Monitor for suspicious exercise: Repeatedly monitor techniques for suspicious exercise, akin to uncommon community connections or course of behaviour.
- Use risk detection instruments: Think about using risk detection instruments, akin to behavioural evaluation and machine learning-based techniques, to detect and reply to threats like OBSCURE#BAT.