A brand new malware menace known as Zhong Stealer has surfaced from China, and it’s already slipping into companies by an surprising entry level – buyer assist chats. This info-stealing malware is presently infiltrating fintech companies by exploiting assist brokers, however the greater concern is its adaptability.
Zhong Stealer can simply be repurposed to focus on any trade that depends on buyer assist groups – hospitality, healthcare, retail, and past. If what you are promoting has a customer-facing group, it may simply be the subsequent goal.
Let’s take a more in-depth have a look at how this malware operates and what companies can do to cease future assaults earlier than they escalate.
How Zhong Stealer Works
Cybercriminals behind Zhong Stealer don’t depend on complicated exploits or high-tech hacking instruments to interrupt into companies. As an alternative, they use a low-effort however extremely efficient rip-off that performs on human nature: urgency, confusion, and frustration.
As famous by ANY.RUN researchers, the assault unfolds in a calculated, repetitive sample designed to put on down buyer assist brokers:
- A brand new assist ticket seems however the sender’s account is model new and fully empty. There’s no historical past, no previous interactions, only a imprecise request for assist.
- The attacker varieties in damaged language, often Chinese language, making the dialog tough to observe. This provides a component of confusion and makes the request appear extra pressing.
- A ZIP file is hooked up, supposedly containing screenshots or different vital particulars for the request. The attacker insists the assist agent should open it to grasp the difficulty.
- If the agent hesitates, the attacker turns into more and more annoyed, pressuring them to behave.
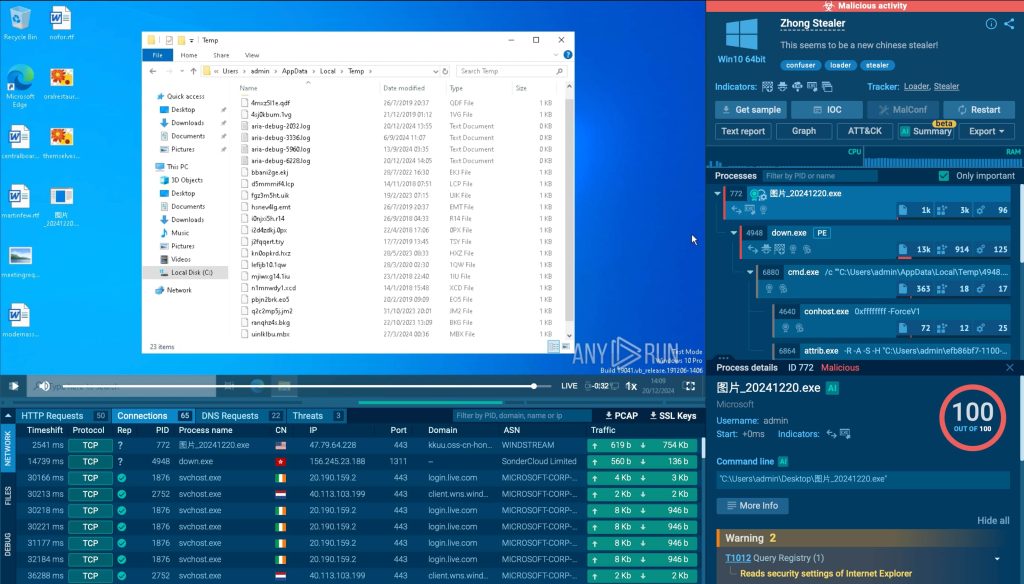
Working Zhong Stealer in a safe and remoted surroundings, such because the ANY.RUN sandbox revealed its behaviour virtually instantly. View the sandbox evaluation right here: Sandbox session with Zhong Stealer
After working the evaluation, we are able to see within the upper-right nook of the display that the ANY.RUN sandbox instantly flagged the file and its actions as malicious, highlighting it in purple.
This permits safety groups to immediately acknowledge threats while not having deep technical experience – the quickest and easiest approach to decide if a suspicious file or hyperlink comprises malware.
| Give your group the ability to establish and cease cyber threats earlier than they unfold. Join a 14-day free trial with ANY.RUN at the moment! Start Your Free Trial |
Through the evaluation session, we are able to additionally see how Zhong Stealer downloads extra elements to proceed the assault:
After all of the preparations, Zhong Stealer begins with credentials theft and information exfiltration. By clicking on the malicious behaviour inside ANY.RUN’s sandbox we are able to see all the principle methods and ways utilized by Zhong Stealer.
From this evaluation, we are able to see how Zhong Stealer maintains persistence on an contaminated system. Its major methodology is including a registry key to guarantee that the malware routinely runs each time the system begins.
If the registry entry is eliminated, Zhong has a backup plan: it makes use of a scheduled process to relaunch itself, making it tougher to completely get rid of.
As soon as persistence is secured, Zhong shifts its focus to the actual purpose: harvesting credentials and browser extension information.
By concentrating on saved login info, it may well steal delicate enterprise and private information earlier than the sufferer even realizes they’ve been compromised.
Lastly, after stealing delicate information, Zhong connects to its command-and-control (C2) server in Hong Kong to ship the stolen info again to the attackers.
Tips on how to Defend Your Enterprise from Zhong Stealer
Zhong Stealer proves that malware can slip into companies by surprising channels, like buyer assist chats.
The simplest approach to test whether or not a file is malicious is to research it with instruments like ANY.RUN sandbox. Due to its user-friendly interface, anybody can use it, even with out technical experience, making it an amazing answer for all group members.
Merely add the file into the safe sandbox surroundings, run the evaluation, and see the decision. If malicious exercise is detected, the file must be reported instantly.
You can too obtain a well-structured report containing all of the assault particulars, making it simpler to share findings with safety groups, IT workers, or decision-makers.
With ANY.RUN, companies can:
- Rapidly analyze suspicious recordsdata and hyperlinks in a protected, managed surroundings with out threat to inner techniques.
- See real-time malware conduct, together with persistence methods, information theft makes an attempt, and communication with exterior servers.
- Determine threats immediately, with flagged malicious exercise highlighted for simple recognition.
- Stop infections earlier than they occur by proactively checking recordsdata earlier than staff open them.