
Which is More Secure for Infrastructure Automation?
Gartner describes infrastructure as code (IaC) as a key way to unlock the potential of the cloud. Nevertheless, some corporations…

Gartner describes infrastructure as code (IaC) as a key way to unlock the potential of the cloud. Nevertheless, some corporations…

The availability chain assault involving the GitHub Motion “tj-actions/changed-files” began as a highly-targeted assault towards considered one of Coinbase’s open-source…
AI techniques have gotten an enormous a part of our lives, however they aren’t excellent. Purple teaming helps discover weaknesses…

Cybercriminals are all the time searching for new methods to benefit from individuals. One efficient technique they use is exploiting…

Counterfeit merchandise are a rising downside in immediately’s market. With developments in expertise, counterfeiters have become more skilled at creating…

Cybercriminals are expert at utilizing public data to their benefit. Understanding how they collect this knowledge might help you defend…
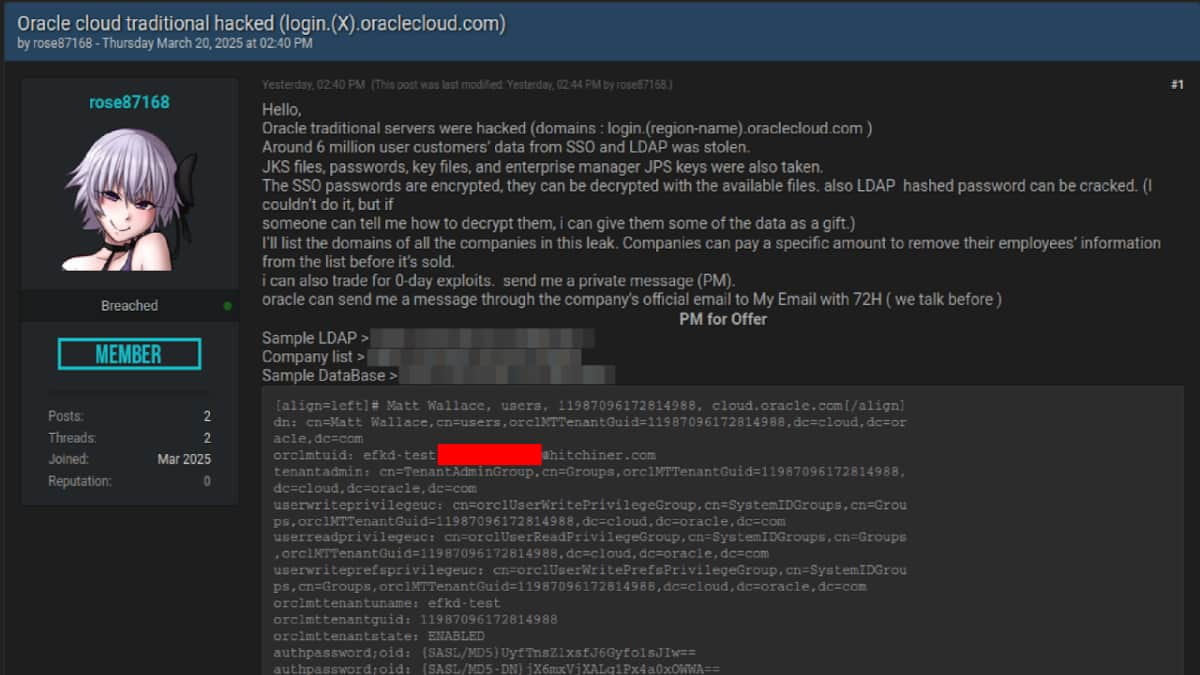
A latest investigation by CloudSEK’s XVigil platform has uncovered a cyberattack focusing on Oracle Cloud, ensuing within the exfiltration of…

Mar 22, 2025Ravie LakshmananMonetary Safety / Cryptocurrency The U.S. Treasury Division has introduced that it is eradicating sanctions towards Twister…
In keeping with new analysis entitled Cyber Safety in Important Nationwide Infrastructure: 2025, from Bridewell, a number one UK-based cyber…
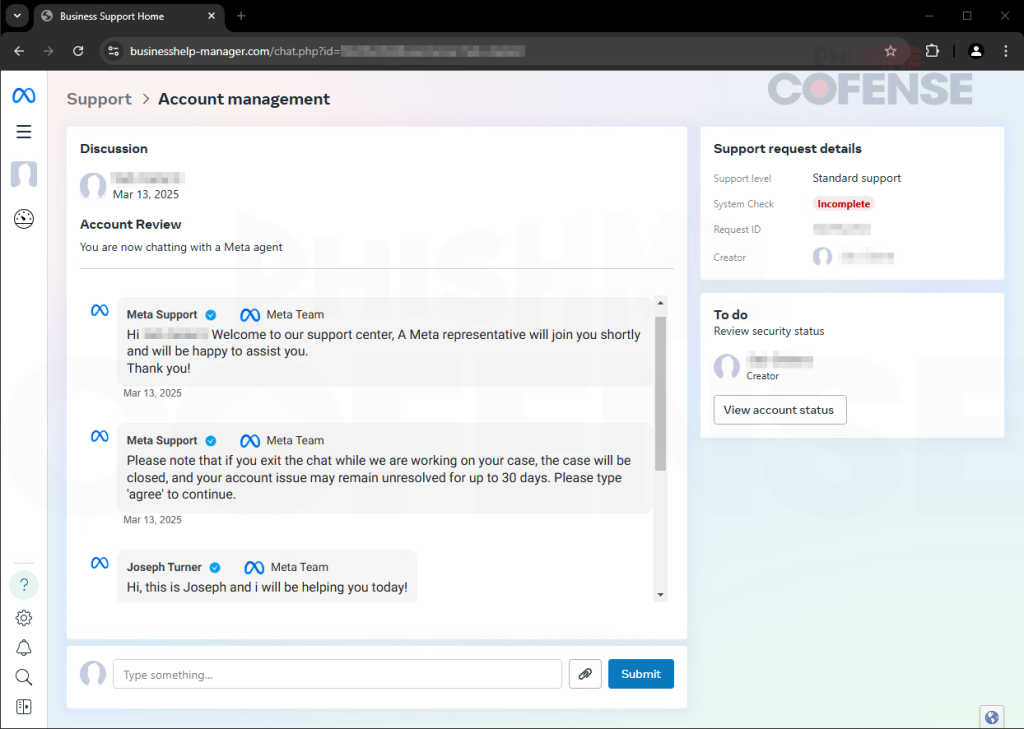
A brand new phishing marketing campaign has been tricking customers into giving out entry to their Meta Business accounts particularly…