
Researchers Link CACTUS Ransomware Tactics to Former Black Basta Affiliates
Mar 04, 2025Ravie LakshmananCybercrime / Menace Intelligence Menace actors deploying the Black Basta and CACTUS ransomware households have been discovered…

Mar 04, 2025Ravie LakshmananCybercrime / Menace Intelligence Menace actors deploying the Black Basta and CACTUS ransomware households have been discovered…

Unit 42 uncovers JavaGhost’s evolving AWS assaults. Find out how this risk actor makes use of phishing, IAM abuse, and…

Boston and Tel Aviv, United States, March 4th, 2025, CyberNewsWire Pathfinder AI expands Hunters’ imaginative and prescient for AI-driven SOCs,…
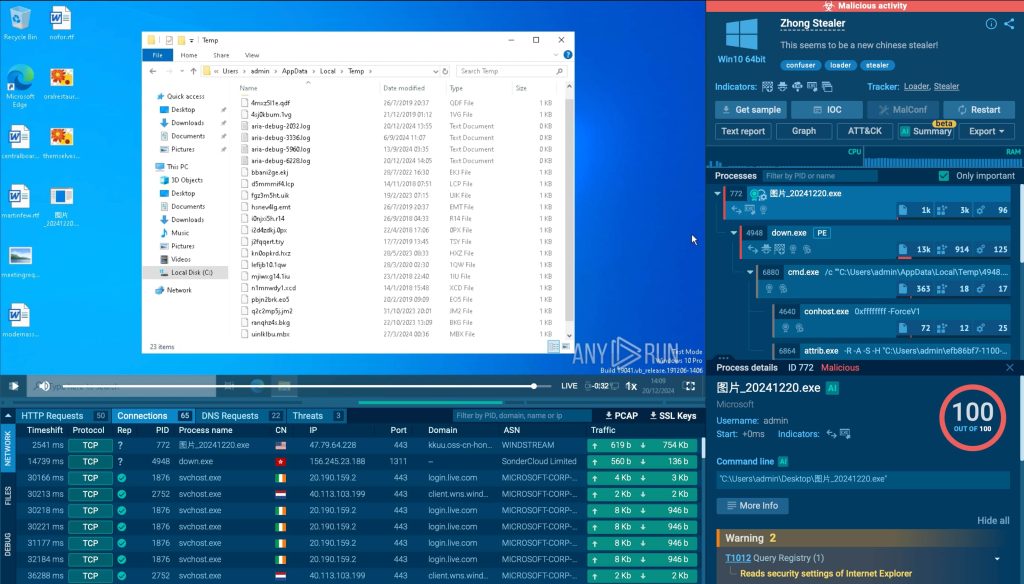
A brand new malware menace known as Zhong Stealer has surfaced from China, and it’s already slipping into companies by…

Credential stuffing assaults had a big impact in 2024, fueled by a vicious circle of infostealer infections and data breaches….

Mar 04, 2025Ravie LakshmananCommunity Safety / Ransomware Web service suppliers (ISPs) in China and the West Coast of the USA…

Mar 04, 2025Ravie LakshmananCyber Espionage / Malware Menace hunters are calling consideration to a brand new highly-targeted phishing marketing campaign…

Mar 04, 2025Ravie LakshmananVulnerability / Cell Safety Google has released its month-to-month Android Safety Bulletin for March 2025 to handle…
The 20 winners of the Most Inspiring Girls in Cyber Awards have been introduced at a ceremony held on the…
Over 70% of entrepreneurs and small enterprise homeowners on the earth immediately use AI for SEO. That’s a staggering quantity….