
Is Your Cloud App Server Secure? Best Practices for Data Protection
Virtually each firm these days is dependent upon cloud computing since it’s a crucial device on the earth of expertise….

Virtually each firm these days is dependent upon cloud computing since it’s a crucial device on the earth of expertise….

A brand new e mail rip-off impersonating cryptocurrency change Binance is tricking customers into downloading malware disguised as a desktop…

Blockchain know-how is revolutionizing industries by enabling secure transactions, decentralization, and transparency. On the identical time, Blockchain software program improvement…

The risk actor often called Blind Eagle has been linked to a collection of ongoing campaigns concentrating on Colombian establishments…

Disgruntled ex-employee sabotages firm programs with malicious code, inflicting main disruptions and monetary losses. Be taught concerning the case and…
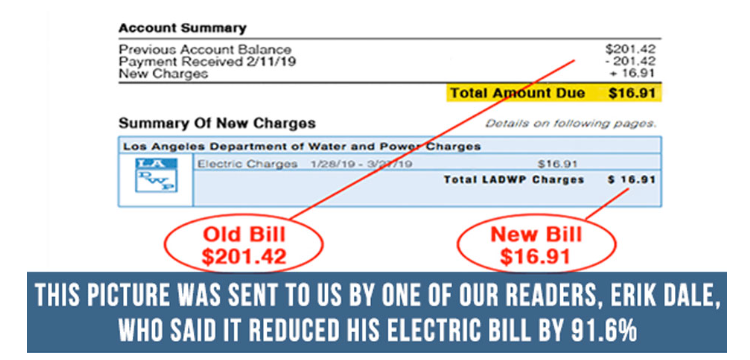
Faux Elon Musk endorsements are utilized in SMS campaigns to promote bogus energy-saving units. Learn to spot these scams and…

Mar 11, 2025Ravie LakshmananCommunity Safety / Vulnerability Unpatched TP-Hyperlink Archer routers have grow to be the goal of a brand…

Mar 11, 2025The Hacker InformationBreach Simulation / Penetration Testing In cybersecurity, confidence is a double-edged sword. Organizations typically function beneath…

Elon Musk has confirmed an enormous cyberattack on his social media platform, X (as soon as Twitter), inflicting widespread technical…

Inside probably the most innocent-looking picture, a wide ranging panorama, or a humorous meme, one thing harmful could possibly be…