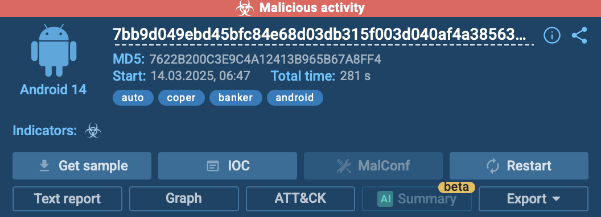
ANY.RUN Introduces Android OS to Its Interactive Sandbox
With Android gadgets deeply embedded in enterprise operations, it’s no shock that cybercriminals are more and more focusing on them….

With Android gadgets deeply embedded in enterprise operations, it’s no shock that cybercriminals are more and more focusing on them….

Mar 18, 2025Ravie LakshmananAdvert Fraud / Cellular Safety Cybersecurity researchers have warned a few large-scale advert fraud marketing campaign that…
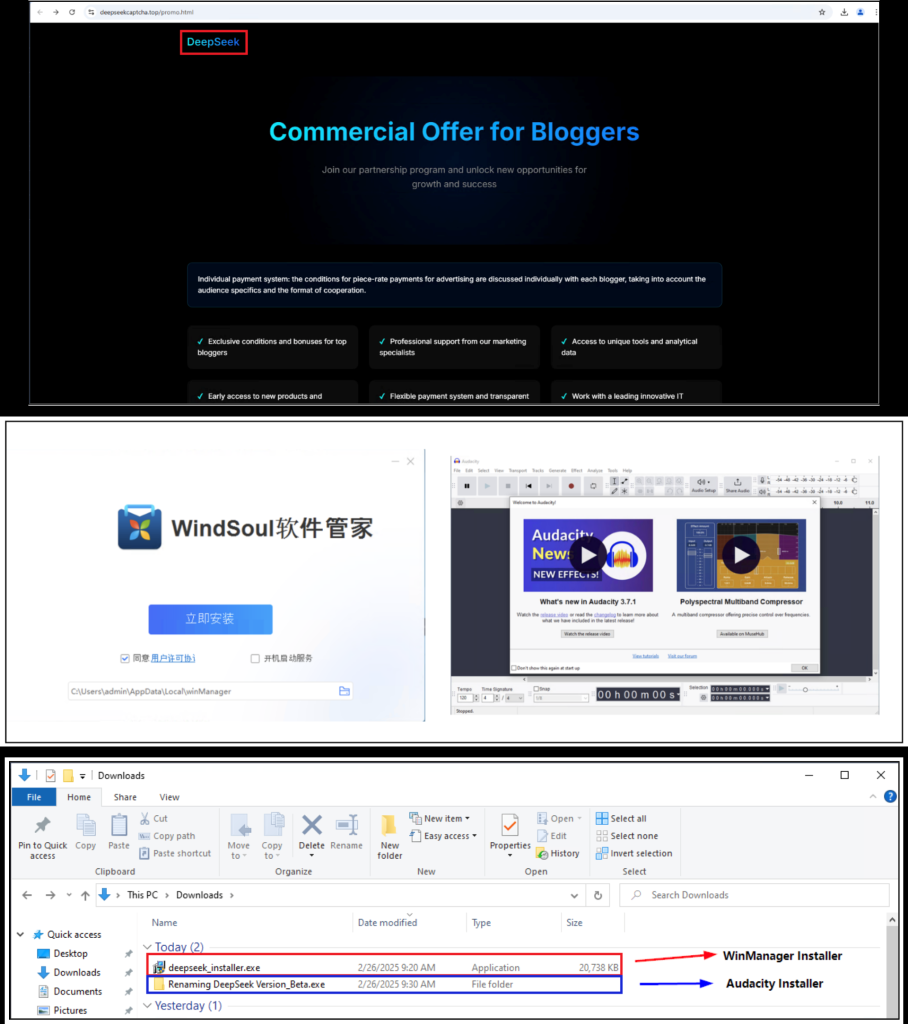
The rise of Artificial Intelligence (AI) has undeniably reworked numerous sectors, with instruments like ChatGPT, DeepSeek and Gemini turning into…
Palo Alto, USA, March 18th, 2025, CyberNewsWire Groundbreaking initiative reveals browser vulnerabilities in understudied but crucial assault floor SquareX, a…
Cybersecurity has a wellbeing downside. One which we, at The IT Safety Guru, gained’t cease shouting about. We’ve all seen…

Mar 18, 2025Ravie LakshmananCyber Assault / Malware A minimum of 4 completely different menace actors have been recognized as concerned…

Mar 18, 2025Ravie LakshmananCyber Espionage / Malware Risk hunters have shed extra gentle on a previously disclosed malware marketing campaign…

Mar 18, 2025The Hacker InformationAuthentication / Identification Safety Whereas Okta gives sturdy native safety features, configuration drift, identification sprawl, and…

Microsoft is asking consideration to a novel distant entry trojan (RAT) named StilachiRAT that it mentioned employs superior methods to…
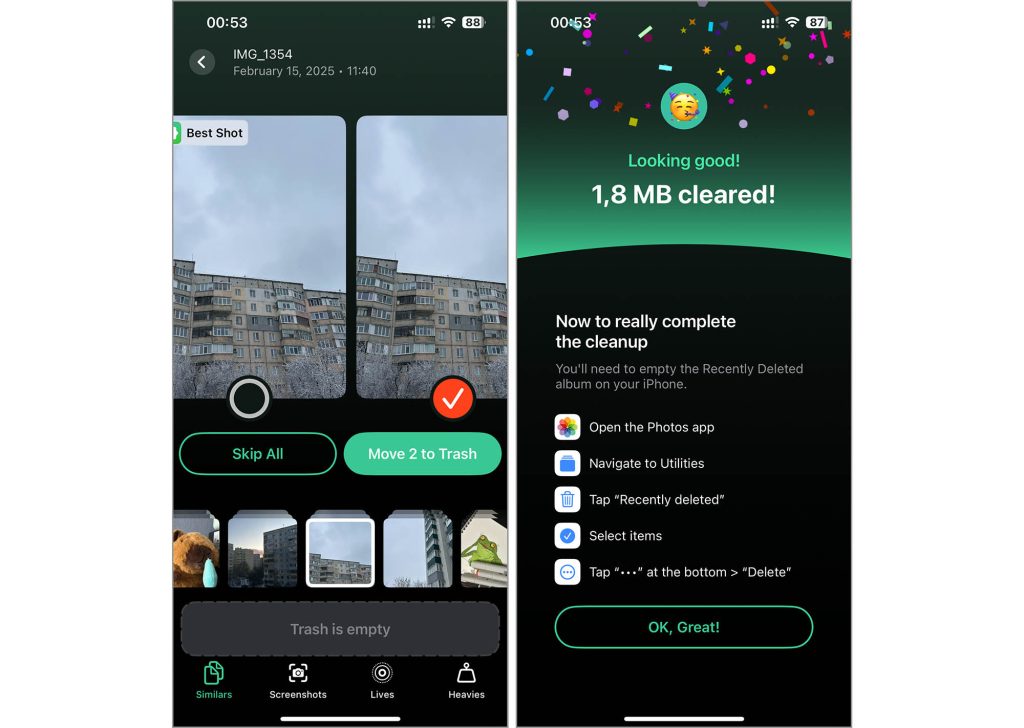
Do you’ll want to completely and securely delete photographs from an iPhone to stop unauthorized access? Merely deleting them isn’t…